In today’s digital world, cybersecurity isn’t just a buzzword, it’s a necessity. We constantly hear about ransomware attacks and data breaches, and it’s easy to feel overwhelmed. But don’t worry, think of it as building a strong safety net for your digital life, so that even when things go wrong, you can bounce back quickly and with confidence.
Understanding the NIST Cybersecurity Framework
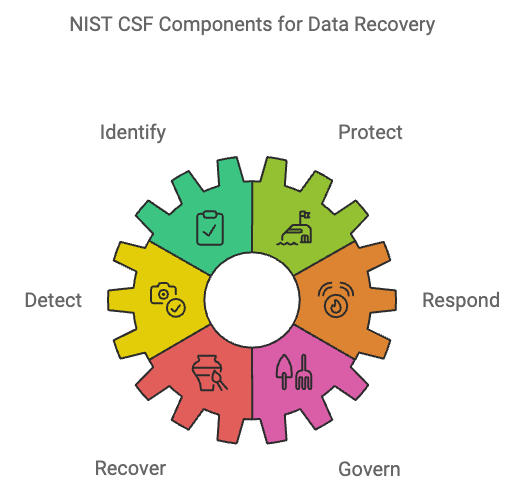
Let’s start by thinking of the NIST Cybersecurity Framework (CSF) as a roadmap. Not just any roadmap, but one that guides you through the twists and turns of keeping your data safe. Imagine you’re driving down a long, winding road, if you know where the tricky turns are, you can navigate better and avoid falling off a cliff. The NIST CSF gives you six key “directions” to follow: Identify, Protect, Detect, Respond, Recover, and Govern. So let’s break them down in simple terms.
- Identify: This is like taking stock of everything in your digital house. You need to know what you have, where it’s stored, and its importance. If you don’t know what you own, how can you protect it?
- Protect: Now that you know what’s in your house, it’s time to build some walls around it. Strong passwords, access controls, and encryption are your brick-and-mortar.
- Detect: Think of this as setting up motion sensors or security cameras around your fortress. You want to know if anything unusual happens as soon as it does.
- Respond: Even if an intruder sneaks in, you need a plan to fight back. This means having a strategy to contain the damage and communicate with the right people.
- Recover: Let’s say things do go south, and your defenses are breached. What’s your recovery plan? Backup systems and processes are your way of hitting the reset button.
- Govern: This is the overseer of your digital kingdom. Think of it like the gardener who tends to the plants, ensuring they thrive and that weeds (aka threats) are quickly dealt with. It’s about having rules, ensuring everyone follows them, and staying vigilant.
Building Your Data Recovery Strategy
Alright, now let’s jump into constructing your data recovery strategy. Imagine it like building a house, a house that can weather any storm. Here’s how you make it sturdy:
1. Laying the Foundation: The 3-2-1-1-0 Rule
The 3-2-1-1-0 rule is like the blueprint for your data recovery house. It’s simple but solid. Here’s what it means:
- 3: Keep at least three copies of your data.
- 2: Store your data on two different media types (e.g., hard drive and cloud storage).
- 1: Keep one copy offsite, away from your primary location.
- 1: Have one copy that’s offline or immutable (that’s just a fancy word for “unchangeable”).
- 0: Ensure you have zero errors in your backups.
Imagine your data is like a valuable jewel. Would you keep all your jewels in one drawer at home? No way! You’d store some in a safe, maybe even send a copy to a vault far away. That’s exactly what this rule does, it ensures that if one or two copies get damaged, you’ve always got a backup ready.
2. Protecting Your Backup Infrastructure
Your backups are like the beating heart of your data recovery plan. And just like you protect your heart with a healthy diet, exercise, and a good security system, you need to do the same for your backup infrastructure. Use things like multi-factor authentication, network segmentation, and least-privilege access to ensure that only the right people have access, and nothing funny happens to your backups.
3. Detecting Threats Early
You don’t want to wait until the storm is tearing the roof off your house to notice something’s wrong, right? The same goes for your data. Early detection is crucial. You want to spot anything fishy as soon as possible, whether it’s unusual file activity, unauthorized access, or changes to your backup configurations. It’s like noticing the dark clouds before the rain starts pouring.
4. Responding Swiftly and Decisively
Let’s say the worst happens, a cyberattack hits. What now? You need to act fast, like a firefighter responding to an alarm. Isolate infected systems, identify where the attack came from, and restore clean data from your backups. It’s like grabbing the hose and putting out the fire before it spreads further.
5. Recovering with Confidence
Your backups are your safety net, your life raft in a storm. But to trust that raft, you need to know it’s reliable and ready. Make sure your backups are regularly tested, up to date, and free of malware. Test your recovery process often, so when the time comes, you know you can bounce back, and fast.
6. Governing Your Cybersecurity Kingdom
Effective cybersecurity isn’t a one-time deal; it’s an ongoing process. You need governance. Think of it as maintaining the health of your kingdom. Establish clear policies, assign responsibilities, and regularly review your security posture. You wouldn’t let a garden grow unattended, right? You need to pull out the weeds (vulnerabilities) regularly and make sure everything is running smoothly.
Bringing it All Together
Cybersecurity, like gardening or building a sturdy house, is something you tend to do over time. You can’t plant a seed and expect it to flourish without constant care. By following these guidelines, and keeping your data recovery strategy up-to-date with the ever-changing world of cyber threats, you can build a resilient system that’ll help you recover from any attack. The NIST CSF is your roadmap, and with a bit of planning, you’ll be back on your feet in no time if the unexpected happens.
The trick isn’t just building strong defenses. It’s building a strategy that ensures you can recover confidently, no matter what life throws at you.