Let’s suppose you’re living in a castle. The walls are high, the moat is deep, and the drawbridge is up. Everything inside is safe, or so you think. This has been how we approached cybersecurity for a long time. We built our digital fortresses and figured we’d be safe inside as long as we kept the bad guys out.
But here’s the thing, what if someone sneaks in? Maybe they’ve got a convincing disguise, or maybe they’ve got a secret tunnel. Suddenly, all that trust we placed in our walls and moats doesn’t seem so secure, does it?
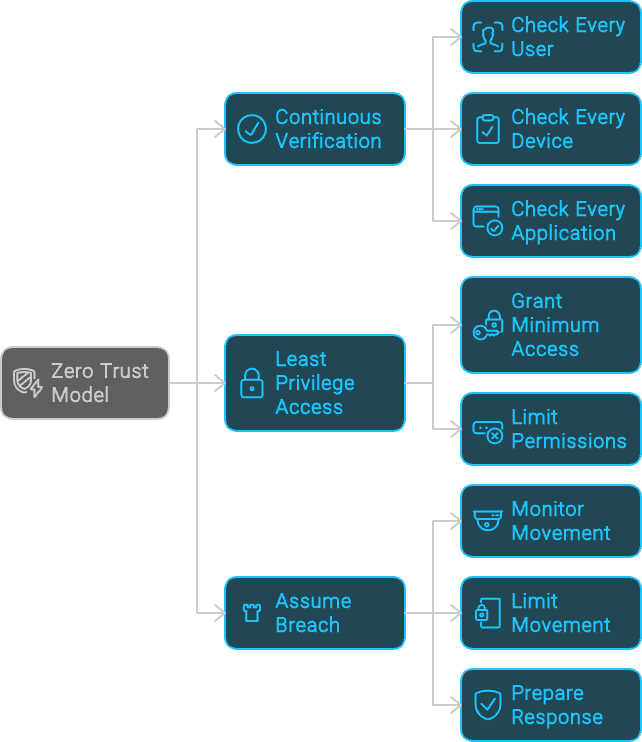
This is where the idea of Zero Trust comes in. Instead of assuming everything inside your castle is trustworthy, Zero Trust says, “Hold on, let’s not assume anything. Let’s check, double-check, and verify everything, every time.”
The Fall of the Castle. Why We Need Zero Trust
Back in the day, the castle-and-moat approach worked because all the important stuff was inside, your data, your applications, your users. But today, the world’s a lot bigger. People are working from coffee shops, data is flying around in the cloud, and your applications are living in all sorts of places. The old moat just doesn’t cut it anymore. It’s like trying to guard a city with just a wooden fence.
So, we flip the script. Instead of trusting what’s inside by default, Zero Trust tells us to start with the assumption that nothing is safe, no matter where it is or who it is. It’s a bit like being a good scientist: question everything, test your hypotheses, and never take anything at face value.
Breaking Down Zero Trust. The Basic Ingredients
Zero Trust isn’t just one thing, it’s more like a recipe. Here are the main ingredients:
- Verify Everything, All the Time: Imagine you’re a bouncer at a club. Every time someone wants to come in, you check their ID, every time, even if you’ve seen them before. That’s what Zero Trust does. It checks and rechecks every user, device, and application, making sure they are who they say they are.
- Give Out the Minimum Keys: Remember when you were a kid, and your parents only let you have the key to your room? They didn’t give you the key to the whole house. In Zero Trust, we do the same thing. We give users just enough access to do their jobs, nothing more.
- Assume Someone’s Already Inside: This might sound a bit paranoid, but it’s practical. Imagine that someone’s already snuck into your castle. Instead of panicking, you calmly limit their movement, monitor them, and prepare to kick them out if they step out of line.
Cooking Up a Zero Trust Strategy
So how do you put Zero Trust into practice? It’s not like flipping a switch, it’s more like renovating a house. You start with the foundation and work your way up.
1. Know What You’re Protecting
First things first, figure out what’s most important. Is it your customer data? Your intellectual property? These are your crown jewels, and they need the most protection. Once you know what you’re guarding, you can start building defenses around it.
2. Divide and Conquer
Next, break your network into smaller chunks. Imagine your castle has many rooms, each with its own lock and key. This way, even if someone sneaks into one room, they can’t just wander into the others. This is called segmentation, and it’s a big part of Zero Trust.
3. Be Picky About Who Gets In
In Zero Trust, you’re like a very picky host. You only let in guests who prove they’re trustworthy, every time. This is where strong identity checks, like multi-factor authentication, come in. It’s like asking someone to show their ID and confirm their invitation before they enter every room.
4. Keep an Eye on Everything
Do you know how detectives are always watching for clues? That’s what you need to do. Keep an eye on all your digital traffic, and look for anything suspicious. Tools like SIEM and EDR are your magnifying glasses, they help you spot trouble before it gets out of hand.
5. Lock Down Your Secrets
Finally, make sure your most important data is locked up tight. Encrypt it so that even if someone gets their hands on it, they can’t make sense of it. And use tools to track where it’s going and who’s accessing it.
The Ups and Downs of Zero Trust
Now, I’m not going to sugarcoat it, setting up Zero Trust isn’t easy. It takes time, effort, and a lot of buy-in from your team. You’re asking everyone to change how they think about security, and that’s no small task.
But here’s the payoff: once you’ve got Zero Trust in place, your castle is a lot harder to breach. You’ve got eyes everywhere, locks on every door, and a plan for what to do if someone sneaks in. It’s like turning your castle into a modern fortress, stronger, smarter, and ready for whatever comes next.
Wrapping It Up. Why Zero Trust is the Future
In a world where threats can come from anywhere, inside, outside, and all around, Zero Trust is the smart, scientific approach to security. It’s not about being paranoid; it’s about being prepared. By questioning everything, verifying everyone, and never taking safety for granted, Zero Trust helps you stay ahead of the game.
Zero Trust isn’t a one-time project, it’s a mindset, a way of thinking about security that evolves as the world around you changes. Start small, build it up, and before you know it, you’ll have a security system that’s as resilient as it is reliable. And in today’s world, that’s something worth striving for.