When you think about Kubernetes, you might picture a vast orchestra with dozens of instruments, each critical for delivering a grand performance. It’s perfect when you have to manage huge, complex applications. But let’s be honest, sometimes all you need is a simple tune played by a skilled guitarist, something agile and efficient. That’s precisely what K3s offers: the elegance of Kubernetes without overwhelming complexity.
What exactly is K3s?
K3s is essentially Kubernetes stripped down to its essentials, carefully crafted by Rancher Labs to address a common frustration: complexity. Think of it as a precisely engineered solution designed to thrive in environments where resources and computing power are limited. Picture scenarios such as small-scale IoT deployments, edge computing setups, or even weekend Raspberry Pi experiments. Unlike traditional Kubernetes, which can feel cumbersome on such modest devices, K3s trims down the system by removing heavy legacy APIs, unnecessary add-ons, and less frequently used features. Its name offers a playful yet clever clue: the original Kubernetes is abbreviated as K8s, representing the eight letters between ‘K’ and ‘s.’ With fewer components, this gracefully simplifies to K3s, keeping the core essentials intact without losing functionality or ease of use.
Why choose K3s?
If your projects aren’t running massive applications, deploying standard Kubernetes can feel excessive, like using a large truck to carry a single bag of groceries. Here’s where K3s shines:
- Edge Computing: Perfect for lightweight, low-resource environments where efficiency and speed matter more than extensive features.
- IoT and Small Devices: Ideal for setting up on compact hardware like Raspberry Pi, delivering functionality without consuming excessive resources.
- Development and Testing: Quickly spin up lightweight clusters for testing without bogging down your system.
Key Differences Between Kubernetes and K3s
When comparing Kubernetes and K3s, several fundamental differences truly set K3s apart, making it ideal for smaller-scale projects or resource-constrained environments:
- Installation Time: Kubernetes installations often require multiple steps, complex dependencies, and extensive configurations. K3s simplifies this into a quick, single-step installation.
- Resource Usage: Standard Kubernetes can be resource-intensive, demanding substantial CPU and memory even when idle. K3s drastically reduces resource consumption, efficiently running on modest hardware.
- Binary Size: Kubernetes needs multiple binaries and services, contributing significantly to its size and complexity. K3s consolidates everything into a single, compact binary, simplifying management and updates.
Here’s a visual analogy to help solidify this concept:
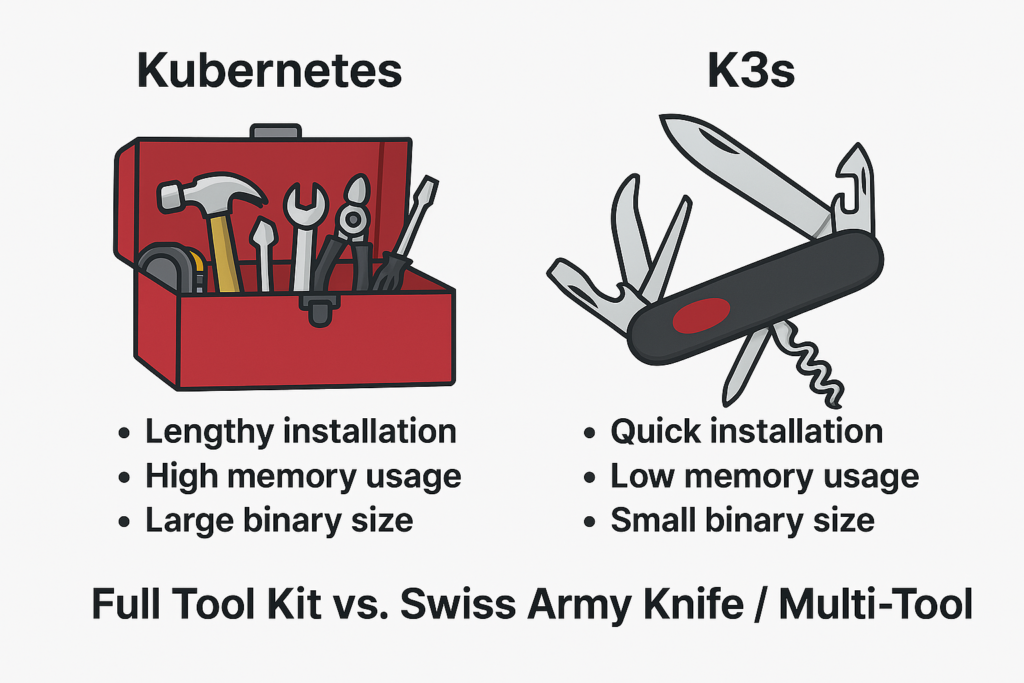
This illustration encapsulates why K3s might be the perfect fit for your lightweight needs.
K3s vs Kubernetes
K3s elegantly cuts through Kubernetes’s complexity by thoughtfully removing legacy APIs, rarely-used functionalities, and heavy add-ons typically burdening smaller environments without adding real value. This meticulous pruning ensures every included feature has a practical purpose, dramatically improving performance on resource-limited hardware. Additionally, K3s’ packaging into a single binary greatly simplifies installation and ongoing management.
Imagine assembling a model airplane. Standard Kubernetes hands you a comprehensive yet daunting kit with hundreds of small, intricate parts, instructions filled with technical jargon, and tools you might never use again. K3s, however, gives you precisely the parts required, neatly organized and clearly labeled, with instructions so straightforward that the process becomes not only manageable but enjoyable. This thoughtful simplification transforms a potentially frustrating task into an approachable and delightful experience.
Getting K3s up and running
One of K3s’ greatest appeals is its effortless setup. Instead of wrestling with numerous installation files, you only need one simple command:
curl -sfL https://get.k3s.io | sh -That’s it! Your cluster is ready. Verify that everything is running smoothly:
kubectl get nodesIf your node appears listed, you’re off to the races!
Adding Additional Nodes
When one node isn’t sufficient, adding extra nodes is straightforward. Use a join command to connect new nodes to your existing cluster. Here, the variable AGENT_IP represents the IP address of the machine you’re adding as a node. Clearly specifying this tells your K3s cluster exactly where to connect the new node. Ensure you specify the server’s IP and match the K3s version across nodes for seamless integration:
export AGENT_IP=192.168.1.12
k3sup join --ip $AGENT_IP --user youruser --server-ip $MASTER_IP --k3s-channel v1.28Your K3s cluster is now ready to scale alongside your needs.
Deploying your first app
Deploying something as straightforward as an NGINX web server on K3s is incredibly simple:
kubectl create deployment nginx --image=nginx
kubectl expose deployment nginx --type=LoadBalancer --port=80Confirm your app deployment with:
kubectl get serviceCongratulations! You’ve successfully deployed your first lightweight app on K3s.
Fun and practical uses for your K3s cluster
K3s isn’t just practical it’s also enjoyable. Here are some quick projects to build your confidence:
- Simple Web Server: Host your static website using NGINX or Apache, easy and ideal for beginners.
- Personal Wiki: Deploy Wiki.js to take notes or document projects, quickly grasping persistent storage essentials.
- Development Environment: Create a small-scale development environment by combining a backend service with MySQL, mastering multi-container management.
These activities provide practical skills while leveraging your new K3s setup.
Embracing the joy of simplicity
K3s beautifully demonstrates that true power can reside in simplicity. It captures Kubernetes’s essential spirit without overwhelming you with unnecessary complexity. Instead of dealing with an extensive toolkit, K3s offers just the right components, intuitive, clear, and thoughtfully chosen to keep you creative and productive. Whether you’re tinkering at home, deploying services on minimal hardware, or exploring container orchestration basics, K3s ensures you spend more time building and less time troubleshooting. This is simplicity at its finest, a gentle reminder that great technology doesn’t need to be intimidating; it just needs to be thoughtfully designed and easy to enjoy.